Share a Policy with a User
Note: The Share option is available only for the Copy from remotely-managed RPS policy.
This section provides information about how to share the Copy from remotely-managed RPS policy with a user.
Important! Before you share a policy with a user, make sure that the user account is initialized.
Follow these steps:
- You can create user in one of the following ways:
- From the Support Page
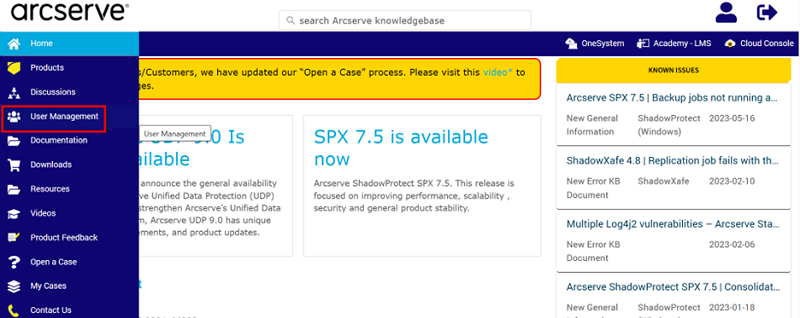
- Log into support.arcserve.com as a Super Admin or MSP Super Admin.
- Click
 .
. - A window appears and prompts you to enter your username and password.
- On the Arcserve Portal, from the left pane, click User Management.
-
- From the Cloud Console UI
- Log into the Cloud Console.
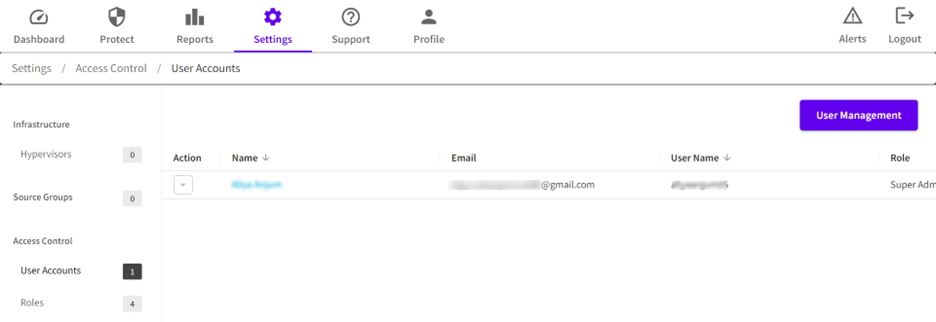
- Navigate to Settings > Access Control > User Accounts.
- On the User Accounts screen, click the User Management button.
-
- The User Management page opens in a new window.
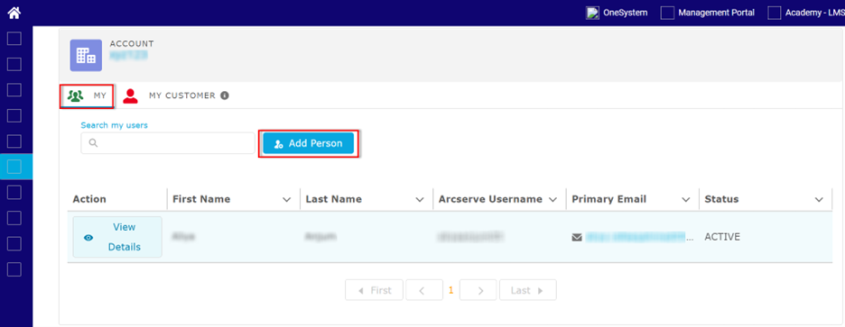
- On the User Management page, do the following:
- Under the MY tab, click Add Person.
-
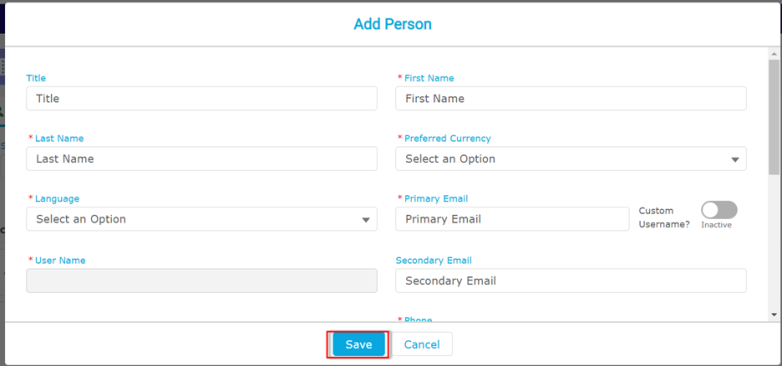
- The Add Person dialog appears.
- On the Add Person dialog, specify details as needed, and then click Save.
-
- The user gets added successfully and appears in the table with the status of the account as INACTIVE.
- Notes:
- By default, the first user gets added with user type as Admin and all the other users get added with user type as User.
- To change the user type, click View Details of the user, click the edit symbol for Cloud Console application, and then select the user type as needed from the drop-down list.
- Click View Details from the Action column of the added user.
- The Account page opens and displays the details of the added user.
- Wait until the account gets provisioned.
-
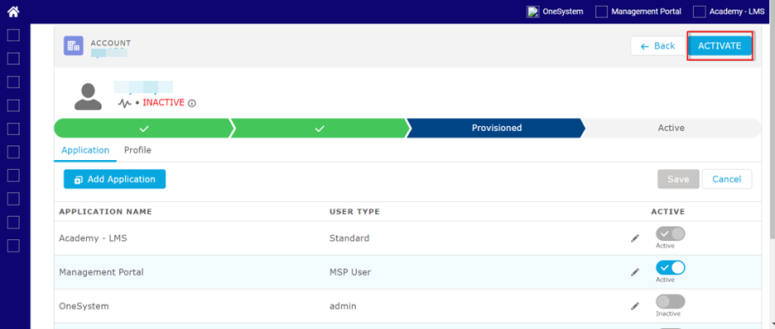
- After the account gets provisioned, Okta will send an email to your primary email address that you have provided while adding the user.
- Open the email that you receive from Okta, and then click the Activate Arcserve Account button to activate your account and set your password.
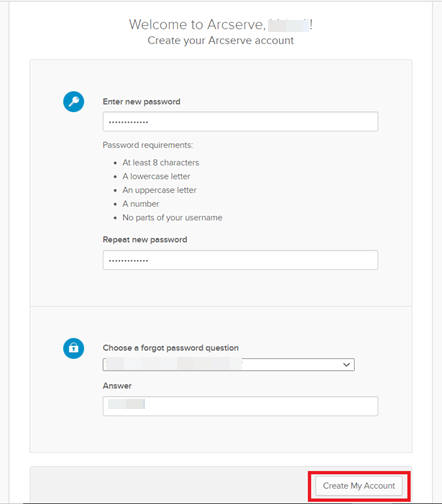
- On the Create your Arcserve account window, do the following, and then click Create My Account:
- Type the new password and then retype the new password to confirm.
- Provide the security details as needed.
-
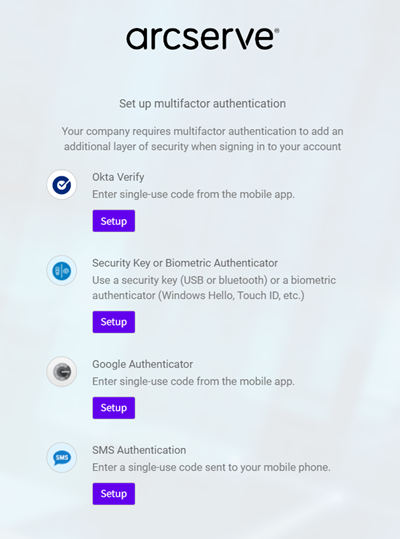
- A window appears and prompts you to set up multifactor authentication.
- Click Setup for the authentication type that you want to select.
-
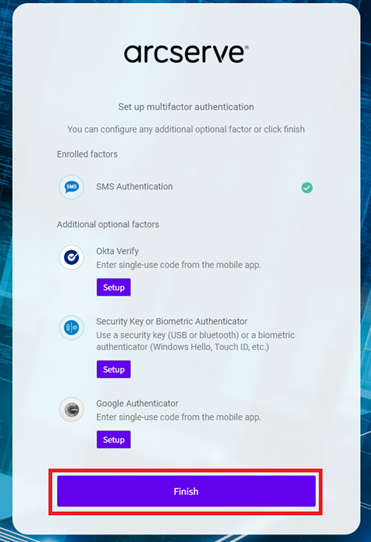
- To complete the multifactor authentication process for the authentication type you have selected, follow the on-screen instructions.
- After you complete the multifactor authentication, click Finish. You can also configure other authentication factors as needed.
-
- You have successfully activated the user account.
- Note: If the Super admin of direct organization creates multiple users of Cloud Console with user type as User, then by default, the Monitor role gets assigned to the added users. Only Super admin can later change the user role to Admin or Recovery.
- All the added users display on the User Accounts page in Cloud Console.
- On the top-right corner, click Cloud Console.
- Navigate to Settings > Access Control > User Accounts.
- From the Action drop-down list of a user that you have created, click Manage Permissions.
-
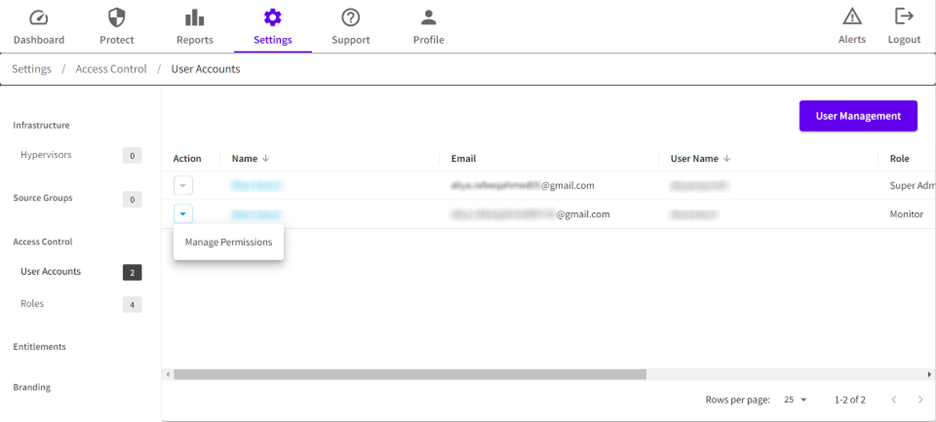
- On the User Permissions for <user name> dialog, from the User Role drop-down list, select the role that you want to assign.
- Click Save.
- Under the MY CUSTOMER tab, click Add My Customer.
-
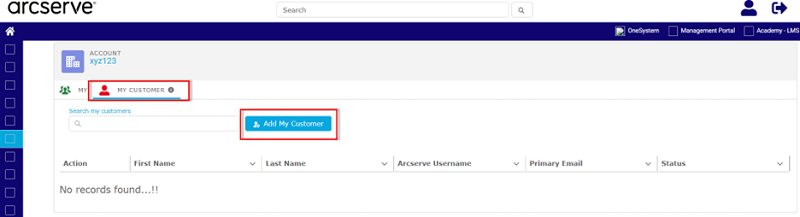
- The Add My Customer dialog appears.
- On the Add My Customer dialog, specify details as needed, and then click Save.
-
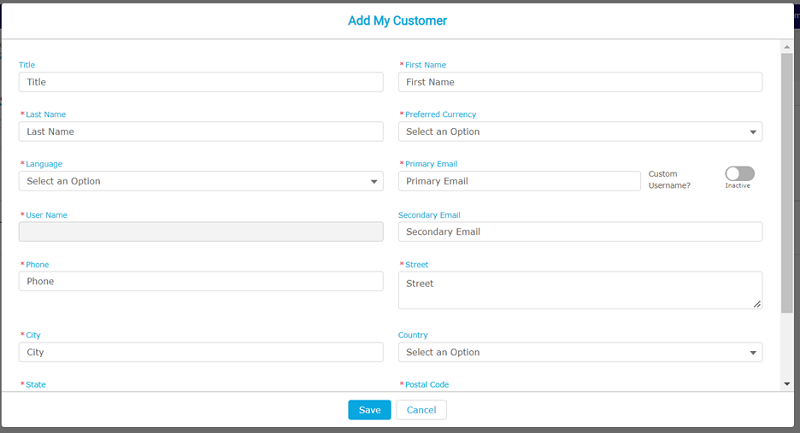
- The customer gets added successfully and appears under the My CUSTOMER table with the status of the account as INACTIVE.
- Note: All the Tenant users get added with user type as External.
- Click View Details from the Action column of the added user.
- The Account page opens and displays the details of the added user.
- Wait until the account gets provisioned.
- After the account gets provisioned, Okta will send an email to your primary email address that you have provided while adding the user.
- Open the email that you receive from Okta, and then click the Activate Arcserve Account button to activate your account and set your password.
- On the Create your Arcserve account window, do the following, and then click Create My Account:
- Type the new password and then retype the new password to confirm.
- Provide the security details as needed.
-
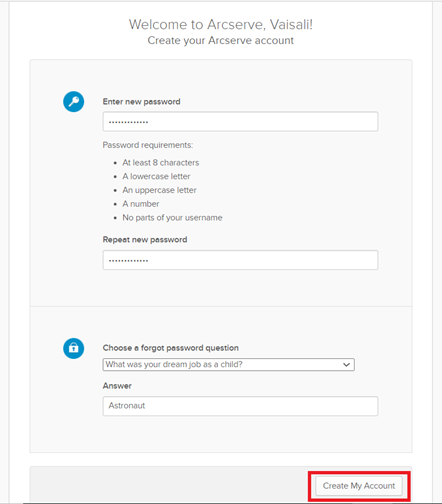
- A window appears and prompts you to set up multifactor authentication.
- Click Setup for the authentication type that you want to select.
-
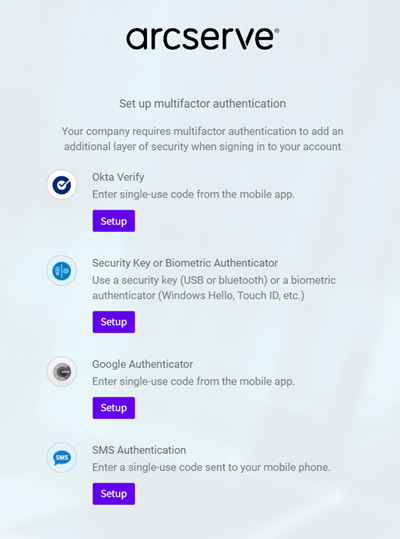
- To complete the multifactor authentication process for the authentication type you have selected, follow the on-screen instructions.
- After you complete the multifactor authentication, click Finish. You can also configure other authentication factors as needed.
-
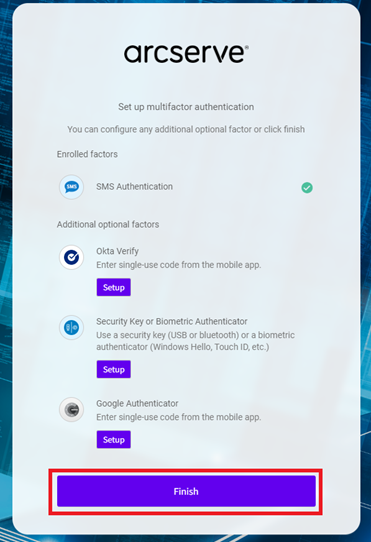
- You have successfully activated your account.
- Note: By default, the Tenant Monitor role gets assigned to the added external user. Only MSP Super Admin can change the role to Tenant Admin or Tenant Recovery.
- All the added users display on the User Accounts page in Cloud Console.
- On the top-right corner, click Cloud Console.
- Navigate to Settings > Access Control > User Accounts.
- From the Action drop-down list of a Tenant user that you have created, click Manage Permissions.
- On the User Permissions for <user name> dialog, do the following:
- From the User Role drop-down list, select Tenant Admin.
- From the Account drop-down list, select the customer account.
- Note: To delete the selected user, click the clear (X) icon on the Account drop-down.
- Click Save.
- Do one of the following:
- If you are a Super Admin, go to Protect > Policies.
- If you are an MSP Super Admin, go to Protect, click the
icon of a customer name, and then click Policies.
- From the Action drop-down list of a policy, click Share.
- The Share Policy dialog appears.
- Type the username of a user you want to share the policy with, and then click Add.
- The user account gets added.
- Notes:
- To add multiple users, repeat Step 3.
- You cannot share the policy with any MSP user.
- Click Save.
-
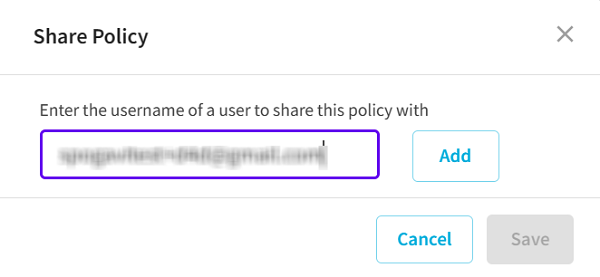
- The policy is shared successfully.
Follow these steps:
You have created the user successfully.
Follow these steps:
You have created the user successfully.