Prepare Environment for HA with the GSSnsupdate Script
To run high availability scenarios in secure DNS Zone domains, you need to configure your UNIX or Linux server so that it is able to authenticate and change the DNS HOST A records for the Master and Replica servers in scenarios.
You may configure your UNIX/Linux environment for Arcserve Continuity Suite using the included script, written by PERL. Contact Support to obtain other versions of this script.
The following steps should be performed on all UNIX/Linux hosts in your environment.
To prepare UNIX and Linux hosts for HA in secure DNS zone domains
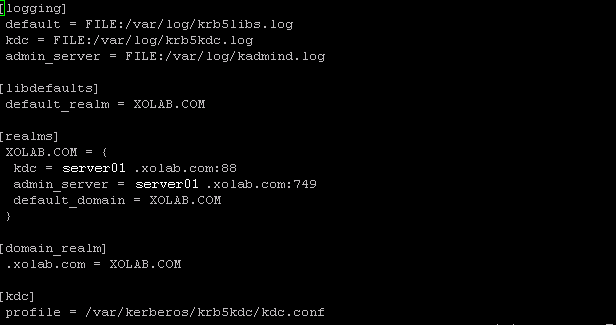
- Configure the Linux host as a Kerberos client. To do this, edit the file, /etc/krb5.conf and make the following changes:
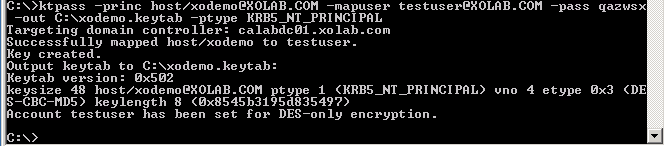
- Create a keytab file with ktpass on the domain controller you specified in "kdc" in the previous step. Log in under a domain admin account on the KDC.
- Transfer the keytab file <filename->.keytab to the Linux host securely.
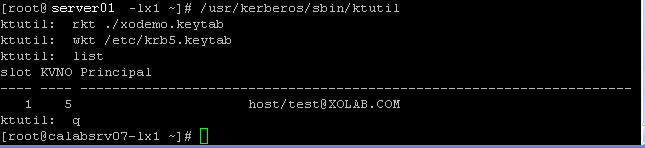
- On the Linux host, combine the keytab file into a single file called, /etc/krb5.keytab, using the ktutil program. You may need to install the Ktutil package first.
- [root@server01-1x1 bin]# ktutil
- ktutil: rkt /root/ <filename->.keytab
- ktutil: wkt /etc/krb5.keytab
- ktutil: list
- ktutil: q
-
- Ensure the Linux host time is synchronized to NTP server or to Microsoft DNS server.
- Copy nsupdate-gss.pl PERL script and install the set of PERL libraries required by the script. These PERL sources can be found at http://search.cpan.org or other RPM.
- perl-Digest-HMAC
- perl-Net-IP
- perl-Net-DNS
- perl-GSSAPI
- perl-Krb5…
- Comment all the following lines in the nsupdate-gss.pl script located in /opt/CA/ARCserve RHA/:
- #############################
- my $sys_retcode = system("kinit -k host/xodemo");
- if ($sys_retcode != 0) {
- print "Failt to create and cache Kerberos ticket through 'kinit'\n";
- exit 1;
- }
- #############################
- Initialize Kerberos cache with the following command:
- Check Kerberos cache with the following command:
- Run the following test to ensure the environment is ready and the script can securely update DNS A records.
- Define the nsupdate-gss.pl script in the ws_rep.cfg file located in the install directory /opt/CA/ARCserveRHA/bin to perform a secure update against Microsoft DNS. Remove the # in front of the "GSSNsupdateScript = " line, as shown below.
- Stop and restart the Engine:
- Repeat this procedure for the other host.
[libdefaults]
default_realm = <DOMAIN name i.e. XOSOFT.ORG>
[realms]
<DOMAIN name> = {
kdc = <DC Server fqdn>:88
admin_server = <DNS Server fqdn>
default_domain = <DOMAIN name i.e. XOSOFT.ORG>
}
[domain_realm]
<domain name >= <DOMAIN name> i.e. .xosoft.org =XOSOFT.ORG
Note: The ktpass utility may not be loaded on Windows by default. You may obtain it from the Windows Support Tools package.
ktpass -princ host/<a name you pick@DOMAIN> -mapuser <domain admin@DOMAIN> -pass <password> -out c:\ <filename->.keytab -ptype KRB5_NT_PRINCIPAL
kinit redhat
redhat is Domain Administrator's account created on the Active Directory.
kinit or kinit –l
./nsupdate-gss.pl 192.168.88.1 shagu01-RHEL5u3-x64 xosoft.org --add_ips=192.168.88.21 --ttl=60 --del_ips=192.168.88.31
####################
# Script for secure update dynamically against MS DNS server on UNIX/Linux hosts
GSSNsupdateScript = "[INSTALLDIR]/scripts/nsupdate-gss.pl"
#
# User can visit arcserve support, or
# define the script by shell or PERL with the arguments matching
# GSSNsupdateScript NAME_SERVER HOST DOMAIN [options]
# Options:
# --add_ips=IPS target IPs for A records to be added
# --ttl=TTL TTL for the added A records
# --del_ips=IPS target IPs for A records to be removed
/etc/init.d/ARCserveRHA stop
/etc/init.d/ARCserveRHA stop