Example to Configure Mutual Authentication
The example scenario in this section explains how to enable mutual (certificates-based) authentication for hosts participating in Arcserve RHA scenario. For example, let us consider simple File Server scenario where data gets replicated from host A to host B. The example has mutual authentication enabled between all Arcserve RHA roles participating in the scenario that includes Control Service, Master engine, and Replica engine.
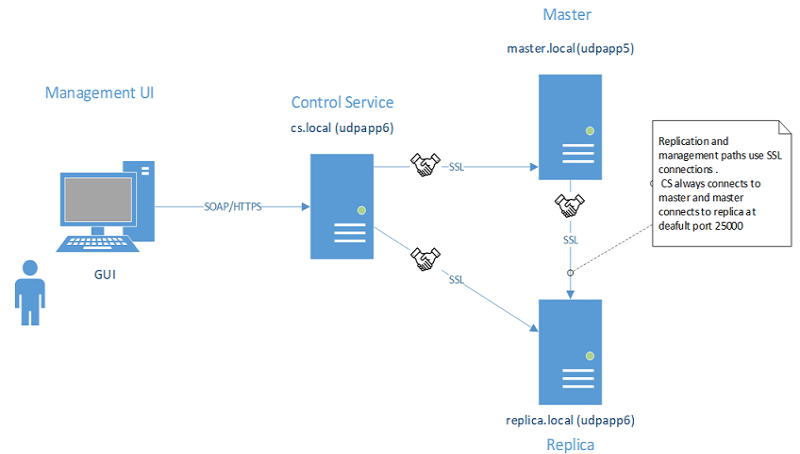
For two hosts to mutually trust each other: Each host must use a valid SSL certificate for establishing management connections, remote peer’s certificate should be added into host’s trusted certificates stores and mutual authentication option should be enabled on each host.
This example has three roles / hosts: Control service (CS), master, and replica. To trust each other, all the three roles need the following:
- Generate valid SSL certificates for CS, master, and replica.
- Configure corresponding role to use the SSL certificate for management connections.
- On each host (role) enable mutual authentication feature and add public certificates of all trusted hosts into role’s trusted certificate store.
Notes:
- For using commercial certificates or own certification authority (CA) to generate certificates, add all certificates from chain of authority into trusted certificate store of role. To verify certificate signed by other certificate / CA, the trusted store of role needs to have public certification of CA / signing certificate.
- For importing several certificates by the PEM file, make one PEM file that only contains just one certificate and import those PEM files one by one.
- All examples in this guide are also valid for UNIX/Linux hosts. For Unix/Linux, use /opt/ARCserve/bin/certutl utility to configure SSL settings for RHA engine. Configuration steps are also similar to those in this example. To restart engine on Linux, use the following command: service ws_rep restart.
The example is explained with the following topics: