Configure IAM Granular Permissions for Service Accounts with VSB to Google Cloud
This section explains the steps and API permission policy required for the Arcserve UDP agent installed on the VSB Cloud proxy within Google Cloud Services. These permissions help you perform the actions required for data transfer and Virtual Standby to Google Cloud. Using this procedure, you can help a Service account get control of and interact with the GCP APIs required to run Arcserve UDP VSB jobs.
The most important step here is to create a service account at the project level, create a custom role, and then associate it to the service account. A role contains a set of permissions that allow the APIs to perform specific actions on Google Cloud resources. The service account and custom role must be created under the project where Arcserve UDP agent is to be installed on the VSB Cloud proxy.
You can use Google Console to create this account and assign the required permissions.
Follow these steps:
- On a web browser, log in to Google Cloud Console as an administrator (the account which has admin privilege to create and manage users/projects/resources) using the following link:
- https://console.cloud.google.com/.
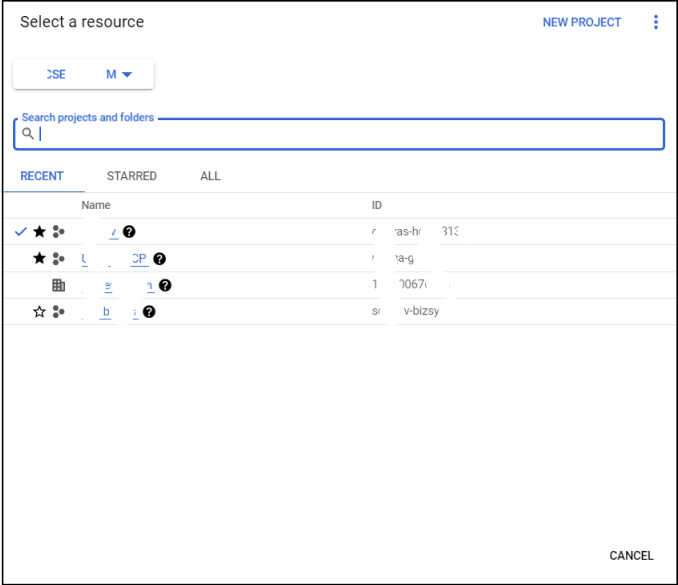
- From the drop-down list at the top left of the page, select the project in which you want to setup VSB cloud proxy.
- If you do not have a project already, click NEW PROJECT to create a new project.
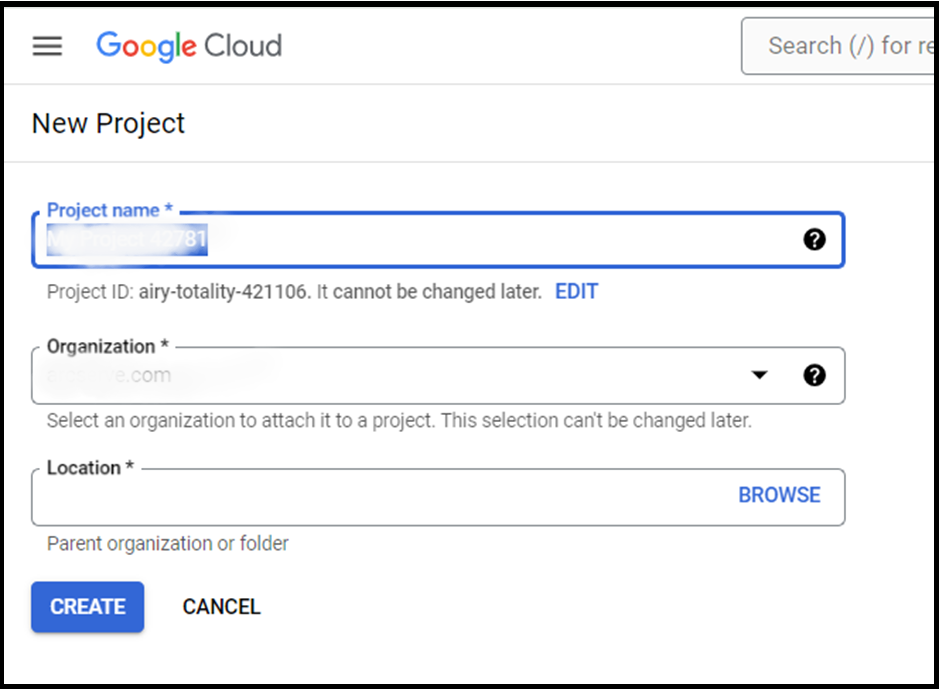
- Enter the values for project name, organization and location and click CREATE.
- After creating the project, select the project on the resource selection wizard menu mentioned in step 2.
- Verify that the desired project dashboard is shown after the project is selected.
- For the Virtual Standby workflows to be successful, the Compute Engine API and Cloud Storage API must be enabled for the project in which the proxy and standby VM are to be created. To enable the APIs:
- In the project dashboard, from the Navigation menu at the top left corner, go to API & Services > Enable APIs & Services.
- In the Search box, enter Compute Engine API, and from the table, select the API and if not already enabled, click Enable API.
- In the Search box, enter Cloud Storage API, and from the table, select the API and if not already enabled, click Enable API.
- Click the Activate Cloud Shell icon
 at the top right corner of Google Console.
at the top right corner of Google Console. - A Cloud Shell Terminal opens at the bottom as shown below.
-
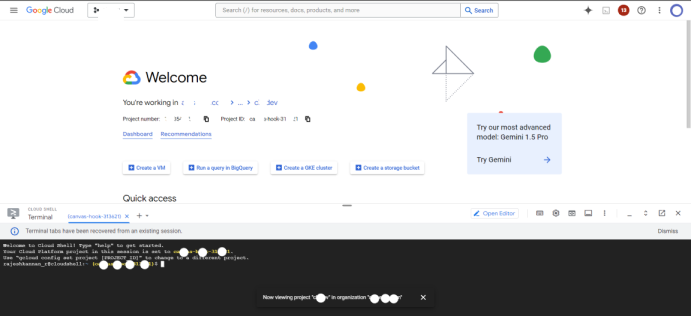
- Validate if the shell is set to the desired project. If it is not set, use the “gcloud config set project [project ID]” command to set the desired project.
- Copy the following command to a notepad, edit the ROLE_NAME to the desired value, then copy the entire command from the notepad file, paste it in the Cloud Shell Terminal prompt and press the Enter key.
- The command will ask for authorization. Authorize the command and to make this change, enter Y and then press the Enter key.
- This command creates a custom role in the project called ROLE_NAME (example: udpvsbroles or UDPVSBRroles1) with the permissions to create and manage instances. Full name of the role is listed as output of the above command and is in the following format:
- Once the custom role is created, close the Cloud Shell and return to the project dashboard.
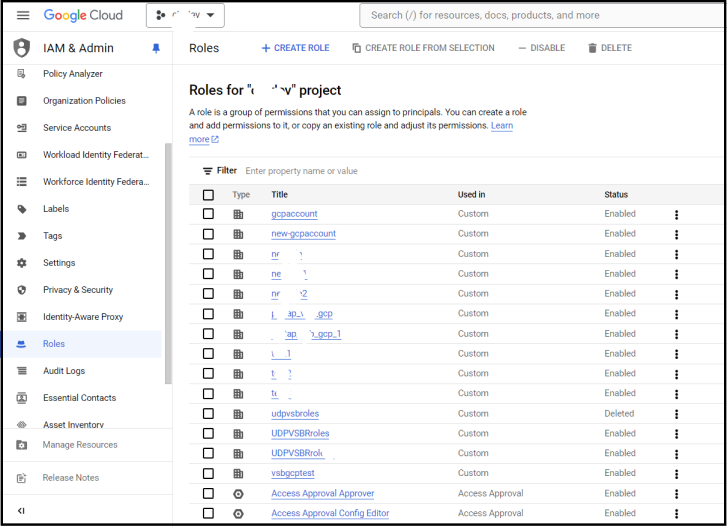
- From the left navigation menu, select IAM and Admin followed by Roles.
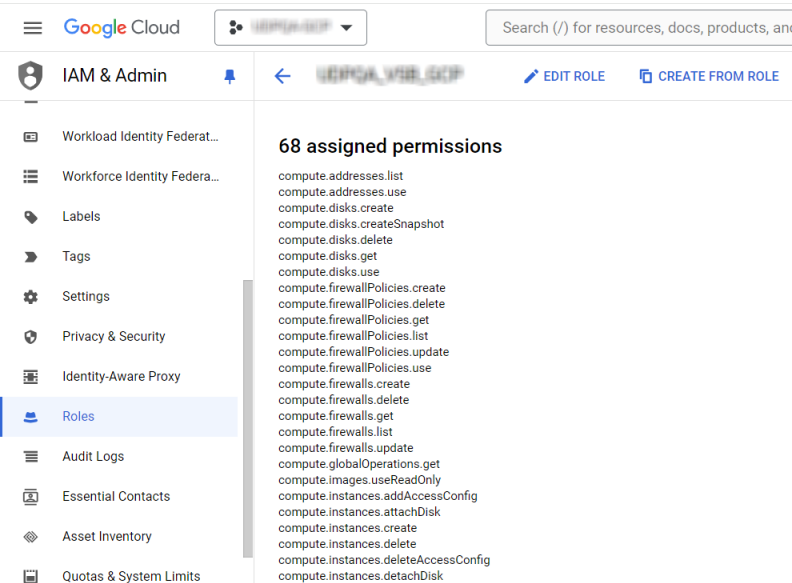
- Verify if the role you just created in Cloud Shell in the previous steps is listed here.
- Click the role and verify if all the 68 permissions are listed.

gcloud iam roles create ROLE_NAME --project=$(echo $DEVSHELL_PROJECT_ID) --permissions=compute.addresses.list,compute.addresses.use,compute.disks.create,compute.disks.createSnapshot,compute.disks.delete,compute.disks.get,compute.disks.use,compute.firewallPolicies.create,compute.firewallPolicies.delete,compute.firewallPolicies.get,compute.firewallPolicies.list,compute.firewallPolicies.update,compute.firewallPolicies.use,compute.firewalls.create,compute.firewalls.delete,compute.firewalls.get,compute.firewalls.list,compute.firewalls.update,compute.globalOperations.get,compute.images.useReadOnly,compute.instances.addAccessConfig,compute.instances.attachDisk,compute.instances.create,compute.instances.delete,compute.instances.deleteAccessConfig,compute.instances.detachDisk,compute.instances.list,compute.instances.setMetadata,compute.instances.setServiceAccount,compute.instances.start,compute.instances.stop,compute.instances.update,compute.instances.updateDisplayDevice,compute.machineTypes.list,compute.networks.access,compute.networks.create,compute.networks.delete,compute.networks.get,compute.networks.getEffectiveFirewalls,compute.networks.list,compute.networks.use,compute.networks.useExternalIp,compute.regionOperations.get,compute.snapshots.create,compute.snapshots.delete,compute.snapshots.get,compute.snapshots.useReadOnly,compute.subnetworks.create,compute.subnetworks.delete,compute.subnetworks.get,compute.subnetworks.list,compute.subnetworks.update,compute.subnetworks.use,compute.subnetworks.useExternalIp,compute.zoneOperations.get,compute.zones.list,iam.serviceAccounts.actAs,iam.serviceAccounts.get,iam.serviceAccounts.list,resourcemanager.projects.get,serviceusage.services.use,storage.buckets.create,storage.buckets.enableObjectRetention,storage.buckets.list,storage.objects.create,storage.objects.delete,storage.objects.get,storage.objects.list
projects/PROJECT_ID/roles/ROLE_NAME
Once the roles are created, you must associate this role to a Service account user. See Create a Service Account and Private Key for more information.