Ad-hoc Virtual Standby to Amazon EC2
The Ad-hoc Virtual Standby machine is created by converting the recovery points to a Amazon EC2 machine format. Standby VM contains same data, same number of disks, and network configurations as Source node.
This section provides the information on how to create an Ad-hoc Virtual Standby Machine on Amazon EC2 cloud.
Notes:
- The Virtual Standby task runs only if the backup task creates a valid recovery point snapshot.
- The Ad-hoc VSB sources will not be listed under Virtual Standby in the left pane of the resources tab.
Follow these steps:
- On the VM(s) Location Step (2 of 4) screen, specify the hypervisor details for the ad-hoc standby VM.
- For Hypervisor Type, from the drop-down list, select Amazon EC2 as the hypervisor.
- For Host, from the drop-down list, select the existing hypervisor or add a new hypervisor.
- To add a new hypervisor, follow these steps:
- From the Host drop-down list, click +Add New Hypervisor.
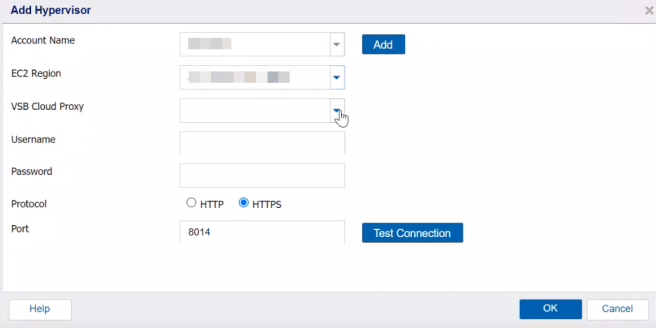
- On the Add Hypervisor dialog, provide the following details as needed and then click OK:
-
- The new hypervisor is added as a host for Ad-hoc Standby VM.
-
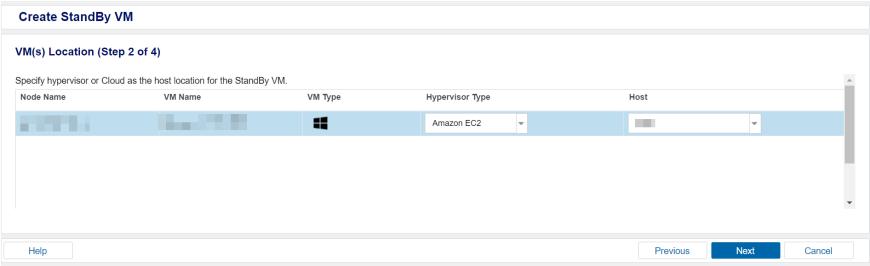
- Click Next.
- The Virtual Machine(s) Settings screen appears.
Account Name
Select the existing Amazon AWS account to access AWS EC2. You can also add a new account by clicking Add. For more information, see Add a Cloud Account for Amazon EC2.
EC2 Region
Specifies the EC2 region where your cloud proxy is located. Arcserve UDP supports all EC2 global regions and EC2 China region.
Note: Make sure to use an administrative account or an account with administrative privileges on the Amazon EC2.
VSB Cloud Proxy
Specifies one EC2 instance in the selected region as the cloud proxy.
Note: The EC2 instance must have Arcserve UDP agent installed.
Username and Password
Specifies the credential to login at the VSB cloud proxy.
Protocol
Specify HTTPS as the protocol that you want to use for communication between the source Arcserve UDP agent on VSB cloud proxy. By default, the HTTPS is selected.
Port
Specifies the port you want to use for data transfer between the Source server and the VSB cloud proxy.
Note: As the cloud proxy is used for data transfer, the related ports must be enabled to access inbound in the AWS EC2 security group, including TCP 8014 and 4091.
Test Connection
Lets you check the connection with the VSB cloud proxy.